There are very few stories. It is the storytelling that counts.
The above statement is very true for movies. I have been a big fan of Disney’s The Lion King. The storyline of Bahubali has a strong resemblance to that of The Lion King, even though the storytelling takes a completely different route and takes gigantic proportions.
| The Good King | Amarendra Bahubali is the good king that is refused the throne and eventually gets killed | King Mufasa is the good king that gets killed |
| The Bad Brother | It is the King’s antagonist brother Bhallaladeva that masterminds the killing of Amarendra Bahubali | It is the King’s antagonist brother Scar that plans the killing of Mufasa |
| The Captive Queen | Devasena is held captive in Maahishmati by Bhallaladeva | Sarabi is forced to hunt for Scar and the hyenas, resembling slavery |
| The Kingdom | Maahishmati: People are sick and tired of Bhallaladeva’s cruel rule | The Pride Lands: The herds and packs are starving and shrinking under Scar’s inept and cruel rule |
| The Far Away Prince | Mahendra Bahubali grows up in a remote place without realizing that he is the prince of Maahishmati Kingdom | Simba runs away and grows up in a remote place without acknowledging his princehood |
| Prince Returns for Love Interest | Mahendra Bahubali searches for his eventual love interest Avanthika and returns to Maahishmati to fulfill her task of freeing Devasena | Simba meets his friend and eventual love interest Nala and that leads to his return to the Pride Lands and freeing of Sarabi |
| The Lookalikes | Mahendra Bahubali’s resemblance to Amarendra Bahubali is the key factor in the story that leads to many scenes with Bhallaladeva, Devasena and Kattappa (in the first part itself.) His resemblance brings cheers to many in the kingdom and fear to the antagonists | Simba’s resemblance to Mufasa and the former’s realization of the same is the key turning point of the story. His resemblance scares Scar and brings joy to Sarabi and rest of the pride rock |
| The Exploring | Mahendra Bahubali, as a kid, wants to explore what is on the other side of the high mountains. He does several unsuccessful attempts as a kid to explore beyond the mountains. Once he becomes successful doing so as an adult, the story takes a new turn | Simba’s exploratory interests are the key part of the story and his attempts end him up in big trouble. That forms the crux of the storyline and his run away from the kingdom |
| The Trustworthy | Kattappa, the trustworthy general and trainer that has bald head and large white beard. Discloses the identity of Mahendra Bahubali to the later and gives him an account of his own past. | Rafiki, the trustworthy shaman and advisor who has bald head and large white beard. Makes Simba realize who he really is and what his responsibilities are. |
| The Pride |  |
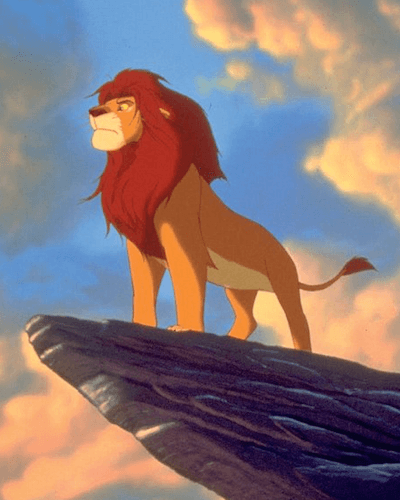 |
| Announcing the Prince |  |
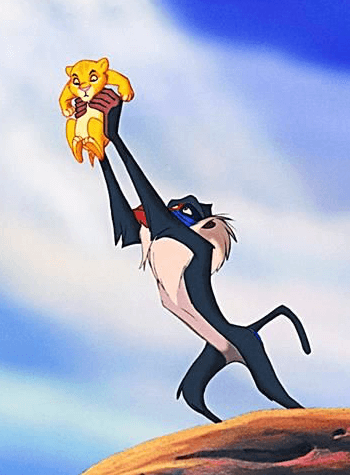 |
Does that make you think that the storyline of Bahubali is lifted from The Lion King? You are very much wrong if you do so. There are several Telugu movies that follow similar lines (Jayam Manadera to Aadi to Indra) where the protagonist lives elsewhere without taking up his true identity and eventually comes back to claim his throne or leadership position. In fact, the faction movie series of Telugu Film Industry have considerable resemblances to The Lion King at some point or other. So are some of the early folk movies of Indian Film Industry. For that matter, all these movies have some resemblance to William Shakespeare’s Hamlet in which Prince Hamlet is true heir of King Hamlet but King Claudius takes the throne.
Then why this post? I strongly believe that the storyline of the movie is of lesser importance when there is good storytelling. On the eve of the release of Bahubali – The Conclusion, I am looking forward to watch a very good storytelling. I care less for the story that I already know of from several other movies.